Paloalto Pan-Os Configuration
LogZilla documentation for Paloalto Pan-Os Configuration
Configure PAN‑OS Syslog
Prerequisites
- Include the device IPv4 address in the syslog header:
Panorama/Device > Setup > Management→Logging and Reporting Settings→Log Export and Reporting→ setSyslog HOSTNAME Formattoipv4-address. - Confirm syslog listener ports in LogZilla (see Syslog Settings).
Create a syslog server profile
- Opens
Server Profiles > Syslogand selectAdd. - A profile Name and Location is specified (Location refers to the virtual system when VSYS is enabled).
- On the
Serverstab, an entry is added with:- Syslog Server (LogZilla IP or hostname)
- Transport (UDP/TCP as required)
- Port (default 514 for UDP)
- Facility (for example,
LOG_USER)
Custom log formats
Threat logs
textPaloAlto_Threat type="$type" src="$src" dst="$dst" rule="$rule" srcuser="$srcuser" sessionid="$sessionid" action="$action" misc="$misc" dstloc="$dstloc" referer="$referer" http_method="$http_method" http_headers="$http_headers"
Traffic logs
textPaloAlto_Traffic type="$type" src="$src" dst="$dst" natsrc="$natsrc" natdst="$natdst" rule="$rule" srcuser="$srcuser" from="$from" to="$to" sessionid="$sessionid" sport="$sport" dport="$dport" natsport="$natsport" natdport="$natdport" proto="$proto" action="$action" bytes="$bytes" packets="$packets" dstloc="$dstloc" action_source="$action_source"
Attach log forwarding
- A
Log Forwardingprofile is created or updated to reference the syslog server profile (Objects → Log Forwarding). - The forwarding profile is applied to the required security policies:
Policies → Security → select a rule → Actions → set
Log Forwardingto the created profile.Log at Session Endcan be enabled as required.
Commit changes
Commit the configuration (Changes → Commit).
Verify in LogZilla
- Reception can be confirmed by searching for the device host or expected text in LogZilla.
- For packet‑level checks, use Syslog Troubleshooting.
LogZilla Rules and Dashboards
Rules and dashboards for Palo Alto are available in the LogZilla appstore
(Settings → App store).
Install the Palo Alto app to enable the rule.

Related topics
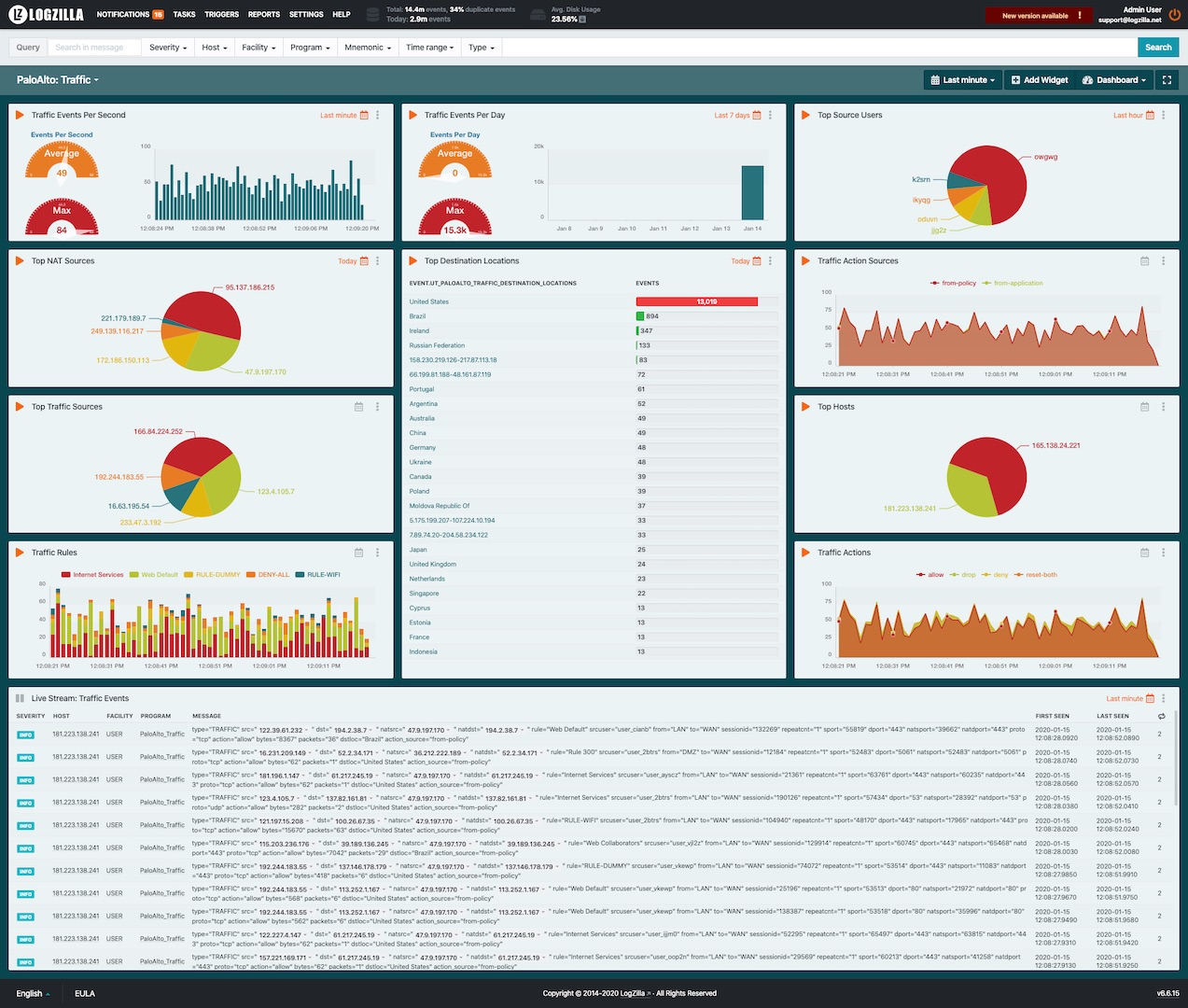
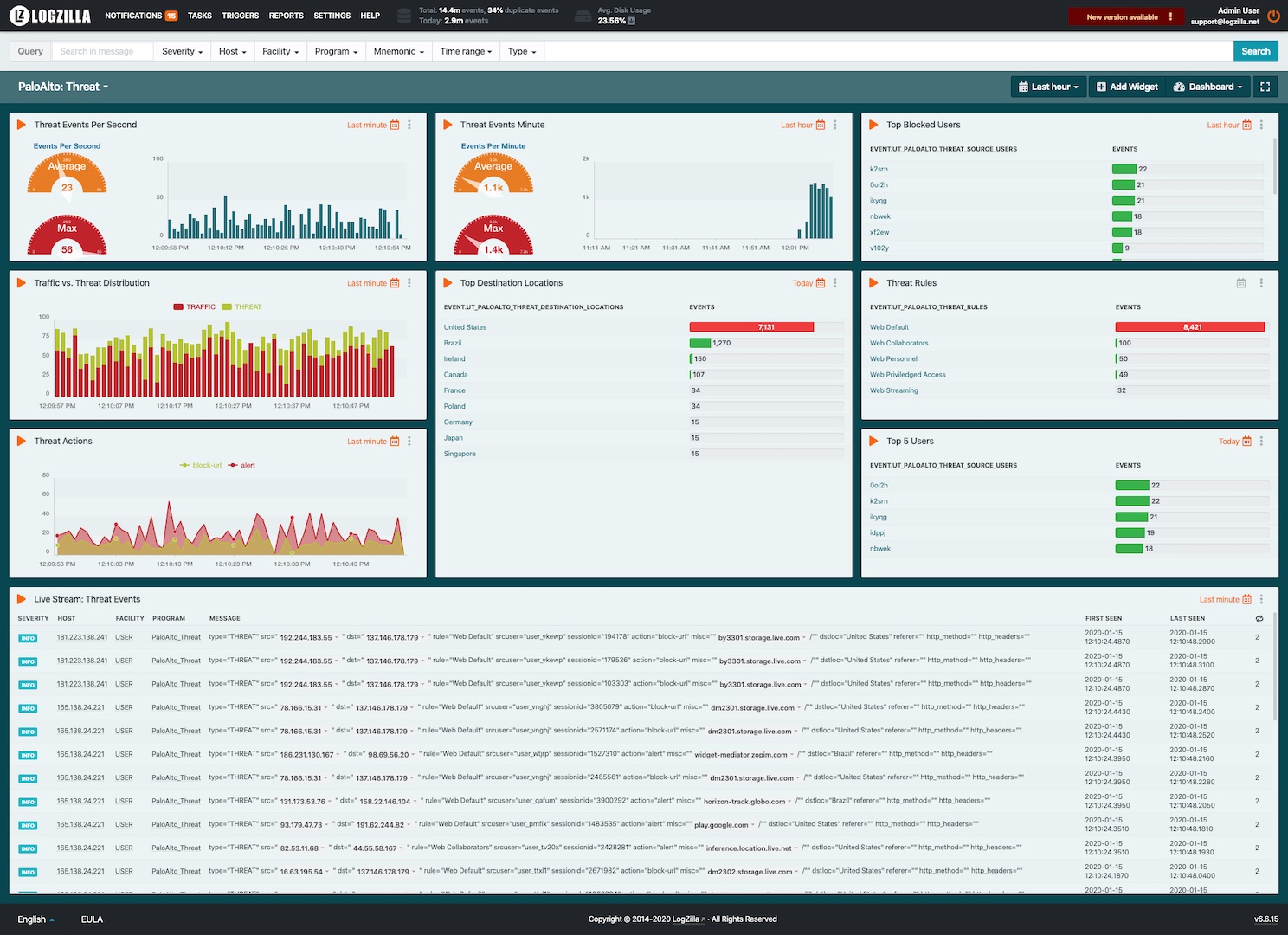
Example dashboards
After installation, the dashboards will look similar to these examples.
Threat dashboard
Traffic dashboard