The Context Crisis: When Every Domain Speaks a Different Language
Modern IT operations span multiple domains, each generating events that lack critical operational context. When incidents occur, teams waste precious minutes manually gathering information that should be immediately available:
NetOps Challenge: "BGP neighbor 203.0.113.1 down" → Which provider? What's the SLA impact? Who handles escalation?
SecOps Challenge: "Authentication failed for user admin" → Is this a brute force attack? What's the user's risk profile? Which assets are at risk?
AppOps Challenge: "Database connection timeout to customer-db" → Which application is affected? What's the business impact? Is failover available?
CloudOps Challenge: "Instance i-0123456789abcdef0 terminated" → Was this planned? What workloads are affected? Is auto-scaling handling it?
DevOps Challenge: "Build failed in customer-portal-pipeline" → Which deployment is blocked? What's the business impact? Who needs notification?
The solution is multi-layered enrichment that transforms domain-specific events into unified operational intelligence at ingest time, eliminating manual context gathering and enabling intelligent automation.
LogZilla's Event Enrichment module enriches events at ingest.
The Multi-Layered Enrichment Architecture
LogZilla's enrichment engine operates through sophisticated layers that build comprehensive operational context:
Layer 1: Device and Asset Context Foundation
Every event begins with identifying its source. LogZilla uses hostname-based lookups to attach rich metadata from your inventory systems, transforming anonymous hostnames into complete operational profiles.
Layer 2: Pattern-Based Event Intelligence
Beyond knowing the source, LogZilla analyzes event content using powerful regex patterns to classify events and attach specific operational metadata including required actions, business impact, and MTTR targets.
Layer 3: Nested Contextual Lookups
The most sophisticated layer uses extracted data from events (like IP addresses, interface names, or user IDs) as lookup keys for additional context, creating deeply enriched events with complete operational intelligence.
NetOps Domain: Network Infrastructure Intelligence
Device Context Configuration
yaml# Network Device Enrichment
- name: Device Context Enrichment
description: Add device context including role, location, contacts, and VRF info
metadata_file: routerMetaData
lookup_field: host
# Router Metadata (routerMetaData.yaml)
R1-CORE-NYC:
Device-Role: Core Router
Location: NYC-DC1
Zone: Production
Contact: Network-Team
Contact-Phone: 555-0101
Criticality: Critical
BGP-AS: 65001
OSPF-Area: 0.0.0.1
Vendor: Cisco
Model: ASR9000
Software-Version: IOS-XR 7.3.2
Management-IP: 10.1.1.1
Backup-Contact: NOC-Escalation
BGP Event Intelligence
yaml# BGP Event Enrichment
- name: BGP Event Enrichment
description: Add context to BGP neighbor state changes and route advertisements
metadata_file: bgpMetaData
lookup_field: message
lookup_re: |
BGP-[45]-ADJCHANGE: neighbor ([0-9\.]+) .* to (up|down)
# BGP Pattern Metadata (bgpMetaData.yaml)
"BGP-4-ADJCHANGE: neighbor ([0-9.]+) .* to down":
Event-Type: BGP-Neighbor-Down
Criticality: High
Required-Action: Investigate
Auto-Remediation: Create Ticket
Documentation: https://internal-docs/bgp-events
Alert-Category: Routing
MTTR: "1-4 hours"
Business-Impact: "Potential Routing Instability"
# Specific Neighbor Context
"203.0.113.1":
AS-Number: "65500"
Neighbor-Role: "EBGP"
Neighbor-Type: "Transit Provider"
Prefix-Count: "Full Table"
Expected-Status: "Up"
Routing-Policy: "Filter Inbound"
Provider: "Level3"
Circuit-ID: "BGP-EXT-001"
Interface Intelligence
yaml# Interface Status Changes
- name: Interface Status Changes
description: Add circuit and criticality info for interface status change events
metadata_file: interfaceMetaData
lookup_field: message
lookup_re: |
Interface ([A-Za-z0-9/\.]+), changed state to (up|down)
# Interface Context (interfaceMetaData.yaml)
"Interface (.*), changed state to down":
Event-Type: Interface-Down
Criticality: High
Required-Action: Investigate
Auto-Remediation: Create Ticket
Documentation: https://internal-docs/interface-events
Alert-Category: Connectivity
MTTR: "1-4 hours"
Business-Impact: "Potential Service Disruption"
# Specific Interface Context
"GigabitEthernet0/0/1":
Circuit-ID: FIBER-NYC-001
Provider: Verizon
Bandwidth: 1Gbps
Service-Type: Internet-Transit
Connected-To: Edge-Firewall
Criticality: High
SLA-Response: 4-hours
NetOps Transformation Example
Before Enrichment: Raw BGP event
text<162>Oct 11 22:14:15 R1 %BGP-4-ADJCHANGE: neighbor 203.0.113.1 Down
After Multi-Layer Enrichment: Complete operational intelligence
json{
"host": "R1",
"message": "%BGP-4-ADJCHANGE: neighbor 203.0.113.1 Down",
"user_tags": {
// Layer 1: Device Context (from routerMetaData.yaml)
"Device-Role": "Core",
"Location": "US-East",
"Contact": "Tony Stark",
"Contact-Phone": "202-555-0101",
"BGP Area": "65001",
"Criticality": "High",
"Management-IP": "10.6.10.1",
// Layer 2: Event Pattern Context (from bgpMetaData.yaml)
"Event-Type": "BGP-Neighbor-Down",
"Required-Action": "Investigate",
"Auto-Remediation": "Create Ticket",
"Alert-Category": "Routing",
"MTTR": "1-4 hours",
"Business-Impact": "Potential Routing Instability",
// Layer 3: Neighbor-Specific Context (from bgpMetaData.yaml)
"AS-Number": "65500",
"Neighbor-Role": "EBGP",
"Neighbor-Type": "Transit Provider",
"Provider": "Level3",
"Circuit-ID": "BGP-EXT-001",
"Expected-Status": "Up",
"Routing-Policy": "Filter Inbound"
}
}
SecOps Domain: Security Intelligence and Threat Context
Security Device Context
yaml# Security Device Metadata
FW-DMZ-01:
Device-Role: Perimeter Firewall
Security-Zone: DMZ
Location: Primary-DC
Contact: Security-Team
Threat-Level: High-Risk
Compliance-Scope: PCI-DSS
Monitoring-Level: Enhanced
SIEM-Integration: Enabled
Incident-Escalation: Security-SOC
Authentication Intelligence
yaml# Authentication Event Enrichment
- name: Security Alert Enrichment
description: Add context to security alerts from ASA firewalls
metadata_file: securityMetaData
filter:
- field: host
op: "=*"
value: ASA
lookup_field: message
lookup_re: |
Authentication failed for user ([a-zA-Z0-9]+)
# Authentication Pattern Metadata
"Authentication failed for user ([a-zA-Z0-9]+)":
Event-Type: Auth-Failure
Security-Category: Identity-Attack
Risk-Level: Medium
Required-Action: Monitor-Pattern
Auto-Remediation: Track-Attempts
Threshold-Lockout: 5-attempts
Investigation-Priority: P3
# User-Specific Context
"admin":
User-Type: Privileged
Risk-Profile: High
Department: IT-Operations
Manager: [email protected]
Last-Login: 2024-01-15
Failed-Attempts-Threshold: 3
Lockout-Duration: 30-minutes
Network Security Events
yaml# Firewall Deny Events
"DENY.*src ([0-9.]+).*dst ([0-9.]+)":
Event-Type: Traffic-Denied
Security-Category: Access-Control
Risk-Assessment: Investigate-Source
Auto-Remediation: GeoIP-Lookup
# IP Asset Context
"192.168.100.50":
Asset-Type: Internal-Server
Business-Function: Web-Application
Data-Classification: Confidential
Owner: Application-Team
Backup-Contact: [email protected]
SecOps Transformation Example
Before Enrichment: Raw authentication failure
textAuthentication failed for user admin from 192.168.100.50
After Multi-Layer Enrichment: Complete security intelligence
json{
"message": "Authentication failed for user admin from 192.168.100.50",
"user_tags": {
// Security Context
"Event-Type": "Auth-Failure",
"Security-Category": "Identity-Attack",
"Risk-Level": "High",
// User Intelligence
"User-Type": "Privileged",
"Risk-Profile": "High",
"Department": "IT-Operations",
"Failed-Attempts-Threshold": 3,
// Source Asset Context
"Source-Asset-Type": "Internal-Server",
"Business-Function": "Web-Application",
"Data-Classification": "Confidential",
"Owner": "Application-Team",
// Response Actions
"Investigation-Priority": "P1",
"Auto-Remediation": "Monitor-Pattern",
"Escalation": "Security-SOC",
"Manager": "[email protected]"
}
}
AppOps Domain: Application Performance and Error Intelligence
Application Context Configuration
yaml# Application Metadata
web-app-prod-01:
Application-Name: Customer-Portal
Environment: Production
Business-Owner: Product-Team
Technical-Owner: DevOps-Team
SLA-Availability: 99.9%
Revenue-Impact: High
User-Base: External-Customers
Database-Dependencies: ["customer-db", "session-store"]
API-Dependencies: ["payment-gateway", "notification-service"]
Database Error Intelligence
yaml# Database Connection Errors
"Connection timeout.*database ([a-zA-Z0-9-]+)":
Event-Type: Database-Timeout
Severity: High
Impact-Category: Service-Degradation
Required-Action: Check-Database-Health
Auto-Remediation: Restart-Connection-Pool
MTTR-Target: "< 5 minutes"
Escalation-Timer: 10-minutes
# Database Context
"customer-db":
Database-Type: PostgreSQL
Cluster-Role: Primary
Location: AWS-RDS-us-east-1
Backup-Available: Yes
Failover-Time: "< 60 seconds"
DBA-Contact: [email protected]
Performance Monitoring
yaml# Response Time Alerts
"Response time ([0-9]+)ms exceeds threshold":
Event-Type: Performance-Degradation
Performance-Category: Latency-Alert
Business-Impact: User-Experience
Auto-Remediation: Scale-Resources
Investigation-Priority: P2
SLA-Breach-Risk: High
AppOps Transformation Example
Before Enrichment: Raw database timeout
textConnection timeout connecting to database customer-db
After Multi-Layer Enrichment: Complete application intelligence
json{
"message": "Connection timeout connecting to database customer-db",
"user_tags": {
// Application Context
"Application-Name": "Customer-Portal",
"Environment": "Production",
"Business-Owner": "Product-Team",
"Revenue-Impact": "High",
"SLA-Availability": "99.9%",
// Database Intelligence
"Database-Type": "PostgreSQL",
"Cluster-Role": "Primary",
"Location": "AWS-RDS-us-east-1",
"Failover-Available": "Yes",
"Failover-Time": "< 60 seconds",
// Business Impact
"User-Base": "External-Customers",
"Dependencies": ["payment-gateway", "notification-service"],
// Response Actions
"Auto-Remediation": "Restart-Connection-Pool",
"MTTR-Target": "< 5 minutes",
"DBA-Contact": "[email protected]",
"Escalation-Timer": "10-minutes"
}
}
CloudOps Domain: Multi-Cloud Infrastructure Intelligence
Cloud Resource Context
yaml# AWS Instance Metadata
i-0123456789abcdef0:
Cloud-Provider: AWS
Region: us-east-1
Availability-Zone: us-east-1a
Instance-Type: m5.large
Environment: Production
Application: Customer-API
Cost-Center: Engineering
Owner: [email protected]
Auto-Scaling-Group: customer-api-asg
Load-Balancer: customer-api-alb
Backup-Schedule: Daily
Cloud Event Intelligence
yaml# Instance State Changes
"Instance ([i-[0-9a-f]+]) state changed to (terminated|stopped)":
Event-Type: Instance-State-Change
Cloud-Category: Compute-Event
Impact-Assessment: Check-Planned-Maintenance
Auto-Remediation: Verify-Auto-Scaling
# Instance-Specific Context
"i-0123456789abcdef0":
Termination-Reason: Auto-Scaling-Down
Expected-Behavior: Yes
Service-Impact: None
Replacement-Available: Auto-Provisioned
Cost and Compliance Context
yaml# Resource Tagging Intelligence
"Cost-Center": Engineering
"Compliance-Scope": SOX
"Data-Classification": Internal
"Backup-Required": Yes
"Monitoring-Level": Enhanced
"Security-Group": web-tier
DevOps Domain: CI/CD and Deployment Intelligence
Pipeline Context Configuration
yaml# CI/CD Pipeline Metadata
customer-portal-pipeline:
Repository: customer-portal
Branch-Strategy: GitFlow
Deployment-Stages: ["dev", "staging", "production"]
Owner: DevOps-Team
Business-Owner: Product-Team
Release-Manager: [email protected]
Rollback-Strategy: Blue-Green
Testing-Requirements: ["unit", "integration", "security"]
Build and Deployment Intelligence
yaml# Build Failure Events
"Build failed.*pipeline ([a-zA-Z0-9-]+)":
Event-Type: Build-Failure
DevOps-Category: CI-Pipeline-Error
Impact-Assessment: Block-Deployment
Auto-Remediation: Notify-Developer
Investigation-Priority: P2
# Deployment Events
"Deployment ([a-zA-Z0-9-]+) to ([a-zA-Z]+) (successful|failed)":
Event-Type: Deployment-Status
DevOps-Category: CD-Pipeline-Event
Business-Impact: Feature-Release
Rollback-Available: Yes
Cross-Domain Correlation and Unified Intelligence
Unified Incident Management
LogZilla's enrichment enables cross-domain event correlation, providing complete operational visibility:
yaml# Cross-Domain Event Correlation
Incident-12345:
Primary-Domain: NetOps
Secondary-Domains: ["SecOps", "AppOps"]
Root-Cause: BGP-Neighbor-Down
Affected-Services: ["Customer-Portal", "Payment-API"]
Security-Implications: None
Business-Impact: Revenue-Loss-Estimated
Coordinated-Response: Required
Business Impact Intelligence
yaml# Business Context Enrichment
"Customer-Portal":
Revenue-Per-Hour: $50000
User-Sessions-Peak: 10000
SLA-Penalty: $5000-per-hour
Executive-Notification: Required-if-P1
Customer-Communication: Marketing-Team
Status-Page-Update: Required
The Dashboard Transformation: Raw Logs to Operational Intelligence
The power of multi-domain enrichment becomes immediately visible in LogZilla's operational dashboards. The screenshot below shows how enriched BGP events appear with complete operational context:
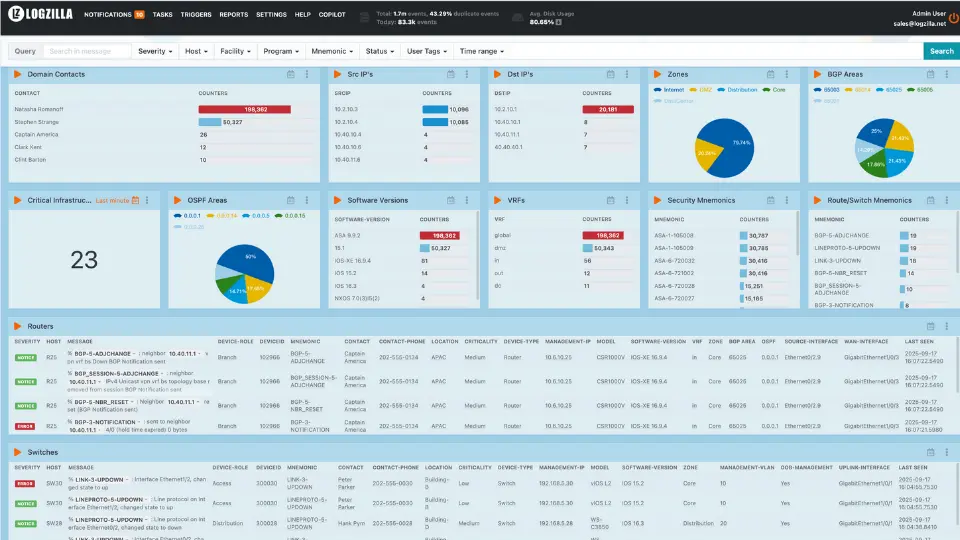
Notice how every event now includes:
- Device Context: Role, location, criticality, and contact information
- Operational Intelligence: MTTR targets, required actions, and auto-remediation steps
- Business Impact: Revenue implications and SLA considerations
- Provider Details: Circuit IDs, contract managers, and escalation paths
This transformation eliminates the manual context-gathering phase that traditionally consumes 80% of incident response time, enabling the advanced event deduplication strategies that reduce alert noise.
Operational Transformation: From Reactive to Proactive
MTTR Reduction Across Domains
| Domain | Before Enrichment | After Enrichment | Improvement |
|---|---|---|---|
| NetOps | 15-30 minutes | 2-5 minutes | 85% reduction |
| SecOps | 20-45 minutes | 3-8 minutes | 80% reduction |
| AppOps | 10-25 minutes | 2-6 minutes | 75% reduction |
| CloudOps | 12-30 minutes | 3-7 minutes | 78% reduction |
| DevOps | 8-20 minutes | 2-5 minutes | 70% reduction |
Automation Enablement
Enriched metadata provides discrete data points for LogZilla's intelligent automation through Triggers configured in the UI:
NetOps BGP Automation Trigger
Trigger Name: "BGP Level3 Outage Response"
Event Match Conditions:
- User Tag:
Event-TypeequalsBGP-Neighbor-Down - User Tag:
ProviderequalsLevel3
Actions:
- Execute Script:
create_vendor_ticket.sh- Script receives event data via environment variables:
EVENT_HOST,EVENT_MESSAGE - User tag values accessible as:
USER_TAG_PROVIDER,USER_TAG_CIRCUIT_ID
- Script receives event data via environment variables:
- Send Email:
- To:
[email protected] - Subject:
BGP Outage: {{event:host}} - {{user_tag:Provider}} - Body:
Circuit {{user_tag:Circuit-ID}} down. Contact: {{user_tag:Contact-Phone}}
- To:
SecOps Privileged User Alert Trigger
Trigger Name: "Privileged User Auth Failure"
Event Match Conditions:
- User Tag:
Event-TypeequalsAuth-Failure - User Tag:
User-TypeequalsPrivileged
Actions:
-
Send Webhook (Slack Integration):
- Method: POST
- URL:
https://hooks.slack.com/services/YOUR/SLACK/WEBHOOK - Post Data:
json{ "text": "🚨 Privileged User Authentication Failure", "attachments": [{ "color": "danger", "fields": [ {"title": "User", "value": "{{user_tag:User-Type}}", "short": true}, {"title": "Risk Profile", "value": "{{user_tag:Risk-Profile}}", "short": true}, {"title": "Department", "value": "{{user_tag:Department}}", "short": true} ] }] }
AppOps Database Failover Trigger
Trigger Name: "Database Timeout Auto-Failover"
Event Match Conditions:
- User Tag:
Event-TypeequalsDatabase-Timeout - User Tag:
Failover-AvailableequalsYes
Actions:
-
Execute Script:
initiate_db_failover.sh- Environment variables:
USER_TAG_DATABASE_TYPE,USER_TAG_FAILOVER_TIME
- Environment variables:
-
Send Webhook (ServiceNow Integration):
- Method: POST
- URL:
https://instance.servicenow.com/api/now/table/incident - Headers:
x-sn-apikey: YOUR_API_KEY - Post Data:
json{ "short_description": "Database Failover: {{user_tag:Database-Type}}", "description": "Auto-failover initiated for {{event:host}}. Expected time: {{user_tag:Failover-Time}}", "priority": "1", "assignment_group": "Database Team" }
Implementation Strategy
Phase 1: Foundation Setup (Weeks 1-2)
Objective: Establish basic enrichment infrastructure
- Inventory Integration: Deploy device/asset metadata across all domains
- Basic Enrichment: Configure hostname-based context enrichment
- Validation: Verify context accuracy and coverage per domain
Phase 2: Domain Intelligence (Weeks 3-6)
Objective: Implement pattern-based enrichment per domain
- Pattern Analysis: Identify high-value event patterns per domain
- Metadata Creation: Build operational context for each pattern
- Auto-Remediation: Configure domain-specific automated responses
Phase 3: Cross-Domain Integration (Weeks 7-8)
Objective: Enable unified operational intelligence
- Event Correlation: Implement cross-domain event relationships
- Unified Dashboards: Create comprehensive operational views
- Business Impact: Configure revenue/SLA impact assessment
Phase 4: Advanced Automation (Weeks 9-12)
Objective: Deploy intelligent operational workflows
- Predictive Alerting: Implement context-based alert prioritization
- Self-Healing: Enable automated remediation workflows
- Continuous Optimization: Implement feedback loops for enrichment tuning
Configuration Architecture
Main Configuration Structure
yaml# config.yaml - Orchestrates enrichment flow
- name: Device Context Enrichment
metadata_file: routerMetaData
lookup_field: host
- name: BGP Event Enrichment
metadata_file: bgpMetaData
lookup_field: message
lookup_re: BGP-[45]-ADJCHANGE: neighbor ([0-9\.]+)
- name: Security Alert Enrichment
metadata_file: securityMetaData
filter:
- field: host
op: "=*"
value: ASA
Metadata File Organization
- Device Metadata:
routerMetaData.yaml,switchMetaData.yaml,serverMetaData.yaml - Event Patterns:
bgpMetaData.yaml,interfaceMetaData.yaml,securityMetaData.yaml - Application Context:
appMetaData.yaml,databaseMetaData.yaml - Cloud Resources:
awsMetaData.yaml,azureMetaData.yaml
Measuring Success: Operational Intelligence KPIs
Response Time Metrics
- Context Availability: 100% of events enriched with operational context
- Manual Lookup Elimination: 95% reduction in external system queries during incidents
- Escalation Accuracy: 90% of incidents routed to correct teams immediately
Automation Metrics
- Auto-Remediation Coverage: 60% of events trigger automated responses
- Ticket Creation Accuracy: 95% of auto-created tickets contain complete context
- Cross-Domain Correlation: 80% of complex incidents show related events
Business Impact Metrics
- Revenue Protection: Quantified business impact assessment per incident
- SLA Compliance: Improved SLA adherence through faster response
- Operational Efficiency: 70% reduction in operational overhead
Advanced Enrichment Patterns
Conditional Enrichment
yaml# Environment-Specific Enrichment
- name: Production Security Events
metadata_file: prodSecurityMetaData
filter:
- field: Environment
op: "eq"
value: Production
lookup_field: message
Nested Lookup Chains
yaml# Multi-Level Context Building
1. Host → Device Context
2. Message Pattern → Event Intelligence
3. Extracted IP → Network Context
4. Service Name → Business Impact
Dynamic Metadata Updates
yaml# Real-Time Context Updates
- Maintenance Windows: Suppress non-critical alerts
- Deployment Events: Correlate with application errors
- Security Incidents: Elevate monitoring levels
Micro-FAQ
How does multi-domain enrichment reduce MTTR?
By adding operational context at ingest time, enrichment eliminates manual lookup steps during incidents. Teams get immediate access to device contacts, business impact, escalation paths, and auto-remediation actions, reducing response time from 15+ minutes to under 2 minutes.
What domains benefit most from log enrichment?
All operational domains benefit significantly: NetOps (network device context), SecOps (threat intelligence), AppOps (service dependencies), CloudOps (resource metadata), and DevOps (pipeline context). Each domain sees 70-85% MTTR reduction.
How does enrichment enable automation?
Enriched metadata provides discrete data points for automation triggers. For example, "Auto-Remediation: Create-P1-Ticket" combined with "Provider: Level3" automatically opens vendor tickets with complete context, eliminating manual escalation steps.
Can enrichment correlate events across domains?
Yes. Cross-domain enrichment enables unified incident management by correlating network outages with application failures and security events, providing complete operational visibility and coordinated response workflows.
Next Steps
Transform your operational intelligence with LogZilla's multi-domain enrichment:
- Assessment: Identify high-impact events across your operational domains
- Pilot Implementation: Start with one domain and measure MTTR improvement
- Expansion: Gradually extend enrichment across all operational areas
- Optimization: Continuously refine enrichment rules based on operational feedback
Ready to eliminate manual context gathering and enable intelligent automation? LogZilla's enrichment engine transforms raw events into complete operational intelligence, reducing MTTR by up to 85% while enabling sophisticated automation workflows across every operational domain.
For organizations seeking to optimize their SIEM costs through intelligent preprocessing or exploring Splunk alternatives, LogZilla's enrichment capabilities provide the foundation for next-generation operational intelligence.